- Platform
- Use Cases
- Company
- Ghost Labs
- Resources
Protect Your Organization Against the OWASP Top 10 API Security Risks
Stay ahead of the constantly evolving threat landscape by fortifying your apps and APIs against modern attacks.
Mitigate security misconfigurations with policy enforcement
API settings misconfiguration can result in unauthorized access and data breaches. Ghost takes proactive steps to prevent security risks by automatically identifying all APIs, even uncovering forgotten or unintentionally exposed ones (known as 'shadow' and 'zombie' APIs). Leveraging the Ghost Platform, organizations gain full visibility into their API landscape and configurations. This empowers them to secure their API settings effectively, aligning with industry best practices, and minimizing the likelihood of security incidents stemming from misconfigurations.
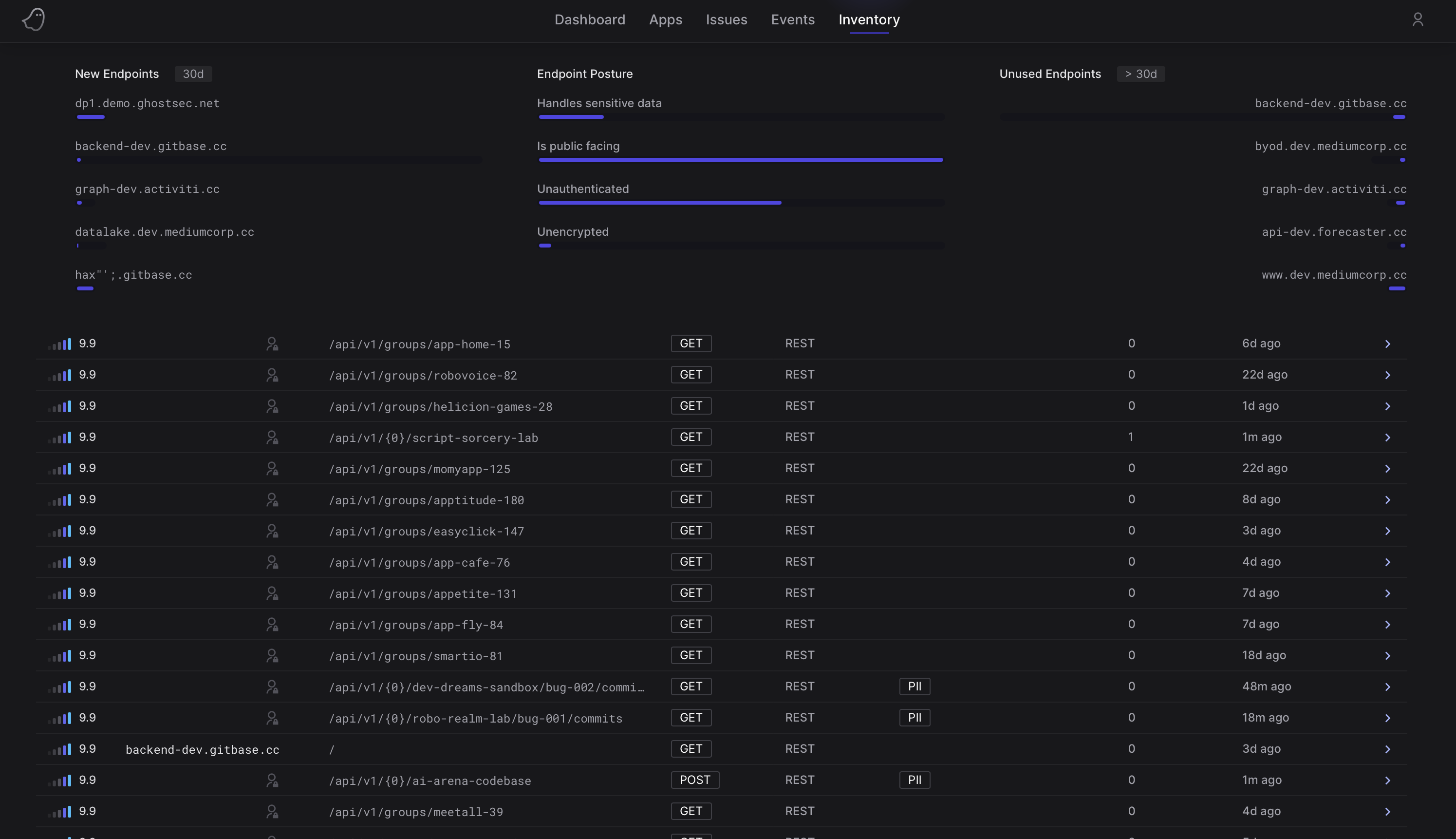
Stay vigilant with continuous monitoring and dynamic anomaly detection, instantly alerting on behavior-based attacks
Traditional security measures are not enough to shield your APIs from the modern API risks outlined by OWASP. API gateways and WAFs (Web Application Firewalls) fall short against the relentless onslaught of intricate attacks that exploit API-specific weaknesses. Enter Ghost, armed with dynamic behavioral analysis and anomaly detection techniques, swiftly pinpointing abnormal patterns or activities signaling malicious intent. Vigilantly monitoring API traffic and user behavior, Ghost swiftly identifies and neutralizes threats like BOLA (Broken Object Level Association) and Unrestricted Resource Consumption, fortifying your defenses with lightning-fast responsiveness.
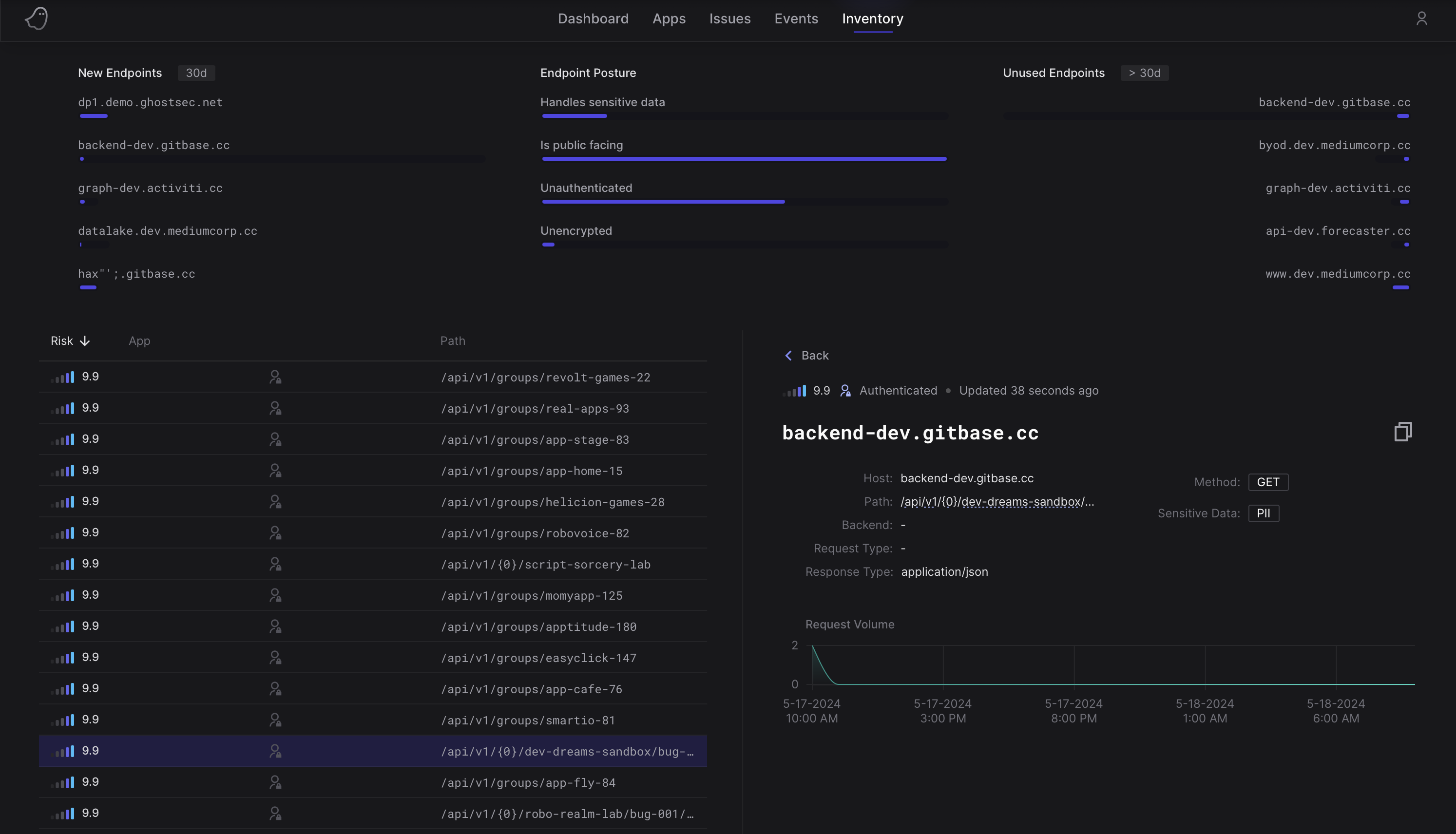
Safeguard data integrity by keeping sensitive information secure
Prevalent API security threats such as Broken Object Property Level Authorization occur when attackers exploit API endpoints to gain unauthorized access to sensitive data. Ghost mitigates this risk by continuously analyzing API endpoint behavior and identifying instances where sensitive data may be exposed. This empowers the Ghost Platform to vigilantly monitor user access, effectively thwarting attackers from tampering with API endpoints to gain unauthorized access or leak sensitive information, thereby ensuring robust data privacy and integrity.
In today's digital world, APIs have become the backbone of web applications and data exchange, making API security a...
