We are proud to introduce Reaper, a sophisticated cross-platform reconnaissance and attack proxy workflow automation tool. Designed to be a modern, resource efficient replacement for similar existing tools, Reaper combines traffic proxy and interception, request tampering, parameter fuzzing, and more into a single solution to enable the user to systematically expose and exploit web application vulnerabilities through a slick, drag-and-drop interface. Now, more of your web application testing activities can be done in a single tool and when you’re done, export and import these workflows to promote collaboration, sharing, and reuse.
So, who and what can benefit from Reaper? Let’s discuss.
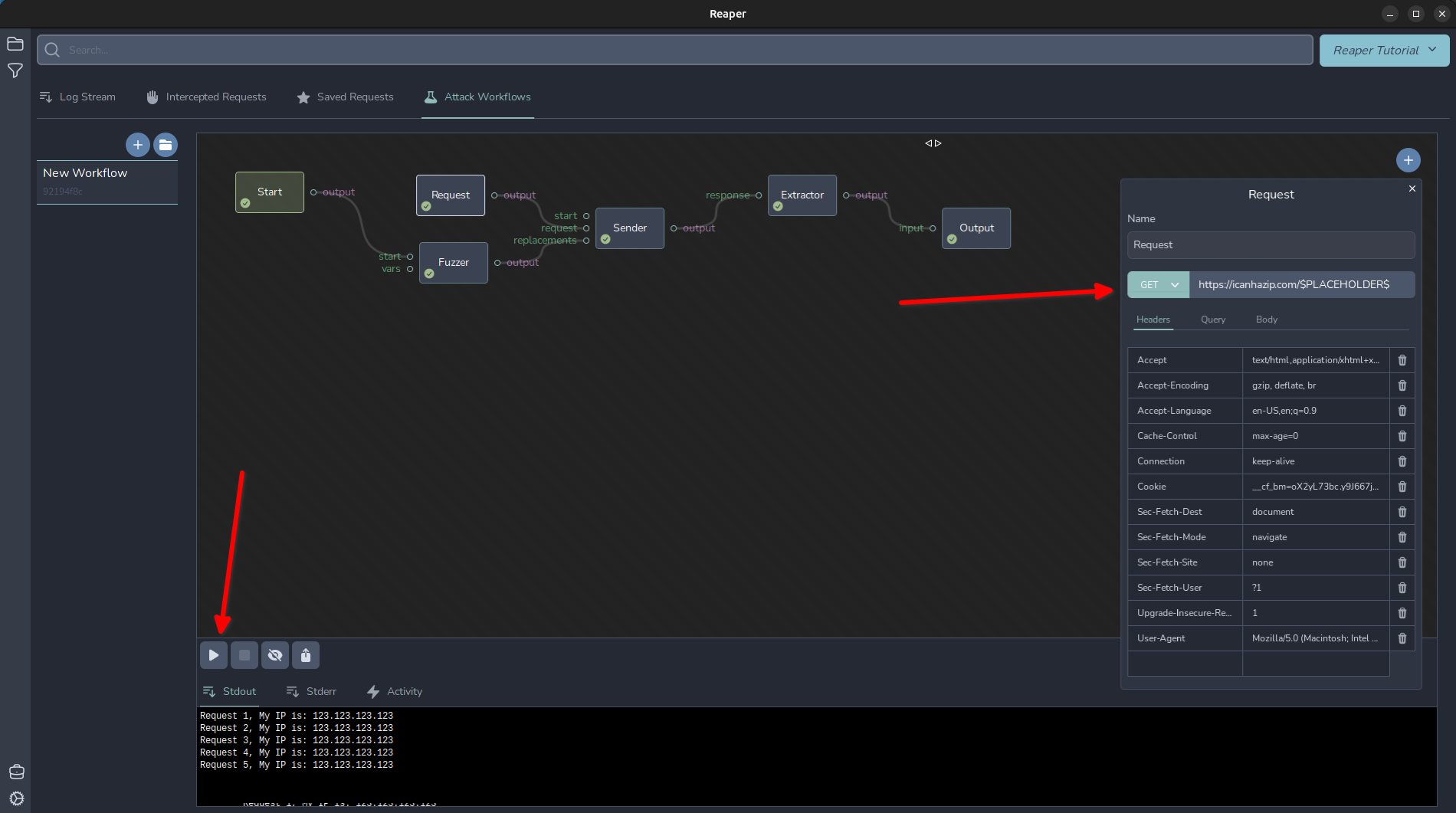
During the reconnaissance stage, Reaper handles the core functionality of traffic proxying, recording, intercepting, and request/response tampering that you would expect. When a sequence of request/responses are deemed to be interesting, they can be "starred" and then automatically converted into a new workflow. This workflow then becomes a visual canvas for drag-and-drop design and execution of sophisticated enumeration and attack sequences. Each logical component leverages a plugin architecture to run custom code snippets for enhanced functionality such as content and parameter encoding, padding payloads to bypass WAF detection, direct manipulation of headers, and much much more. When it comes time for documenting your findings and tools used to exploit a flaw, exporting the workflows into a JSON format can more easily and portably communicate the steps taken to reproduce an issue.
Having the ability to import a previously created workflow into Reaper makes it extremely easy to validate the finding while inspecting every request/response pair. This is a game changer when it comes to internally conveying impact and priority of remediation. For developers of these applications, they can now run Reaper workflows in their CI/CD pipelines against test instances for new builds to validate known findings have not regressed. For the community, this means an easy and repeatable method for sharing exploit workflows.
With Reaper, now everyone in the organization can leverage the value of sophisticated attack workflows without having to be an expert.
Let me walk you through how exactly Reaper came to be, as well as some of the ways we continue to use it here at Ghost. To start, let's put you in my position. It's your first day on the engineering team at Ghost Security. You've finished the HR paperwork, set up your machine, and your first task has been assigned: rob a bank and empty your colleagues’ accounts.
“Say what?”
Not an actual bank. This is where Ghost Bank enters the chat. Ghost Bank is a CTF challenge we've built to demonstrate various API security vulnerabilities. It's a banking web application backed by an API with a real database behind it with real users, real vulnerabilities, and not-so-real money. Now back to our assignment. The goal of said assignment is to steal as much money as possible from the bank, and then write up a report on how you did it.
Image 1: Ghost Bank Interface
Without giving the solution away, you'll need to do some reconnaissance, find a vulnerability, and exploit it. There's no fixed way to go about it, and a variety of tools and techniques can be used. The challenge is designed to be open-ended, and to encourage you to think creatively.
When I first solved the challenge, I used Burp Suite to find my solution, and I wanted to show the team how I did it. Screenshots of Burp seemed to fall a little short when it came to showcasing the methodology, so I decided to build a tool to demonstrate the exploit. I wanted to show the requests I made, the responses I got back, and the vulnerabilities I found. I initially wrote a small Go program, but it was a little clunky, and it wasn't obvious what was going on while it was running. Additionally, I needed to be able to reconfigure things on the fly. From time to time, the challenge resets, and all the bank accounts have their balances restored. I needed to be able to quickly change parameters and rediscover values for a successful exploit, and easily re-run it. I also wanted to be able to send the exploit to my colleagues, so they could see how I did it, and have it be easy for them to run it themselves.
I drew a flow chart of the steps I took to solve the challenge, and I realized that what I really wanted was to be able to:
- build a workflow in this visual fashion
- plan out my exploit as a flow chart and then hit a "run" button
- easily drag and drop steps and reconfigure components of the exploit
- run the exploit and see it progress visually
- see the requests and responses as they happened and pause the exploit at any point, and inspect the state of the application
- share the exploit with my colleagues, and have them be able to run it themselves, and see the same thing I saw.
Explaining how I solved the challenge was one thing, but having a colleague see it run for themselves and understand the flow of the exploit was another. This seemed like a great way to share knowledge and techniques.
This is how Reaper was born. I wanted to take ideas from tried and tested tooling like Burp, and combine them with the automation and collaborative power of tools like Tines.

Image 2: Sample Tines Workflow
I built an initial proof of concept that allowed the drag-and-drop construction of a Ghost Bank exploit using Wails (https://wails.io/) by Lea Anthony. Wails is an awesome project for building desktop applications in Go. It works across Mac, Windows and Linux, and utilizes webviews, meaning a front-end framework of your choice can be used - I chose Vue.
Using this tool, I found an additional unintended vulnerability in the bank and was able to steal more money than existed in the platform, thanks to the speed at which the tool executed exploiting a race condition in the app’s transaction logic.

Image 3: Prototype Reaper Workflow GUI
I presented this initial version at our first in-person company meeting of the year. The headline features were:
- intercept and modify HTTP requests and responses
- save and categorize HTTP requests/responses for later examination/reuse
- manage multiple projects and project-specific settings using workspaces
- incrementally craft workflows to attack web applications using our unique GUI
- automate simple tasks like fuzzing, brute-forcing, and more.
- perform automated attacks against web applications
- create, share and collaborate on custom workflows to automate your testing
- parameterize attacks to make an exploit reusable in a new environment with a couple of clicks and tweaks to some inputs.
Our researchers were excited by the potential to streamline and standardize their internal workflows supporting detection development and testing, and the wider team had some great ideas for further development.
We find Reaper useful internally at Ghost for quickly sharing exploits and reproductions as it allows the person who found and exploited an issue a way to package that expertise into a workflow that anyone on the team can run in seconds. It's also handy for triggering specific detections and testing our API security platform, and we can see plenty of use-cases and new features outside the Ghost universe too.
- Sharing and collaborating on bugs. Package exploits and share them.
- This could be useful for demonstrating vulnerabilities when making bug reports. It's a useful way to demonstrate how exploits work and show what's going on throughout the process. Imagine if the standard for a bug bounty report included a packaged exploit workflow that walked through the attack process and diagramed the approach.
- Plugin system to allow easy extension of workflow functionality e.g. a JWT plugin for encoding/decoding JWTs or automating common JWT attacks.
If you want to see a quick demo of Reaper’s initial features, including the construction of an attack workflow, check out this demo video: Ghost Security's Reaper Overview
Perhaps you have some further ideas? Please tweet us @ghostsecurityHQ or raise an issue on the repo and let us know!
We'd love you to try Reaper out and let us know what you think using GitHub issues. You can download Reaper from https://github.com/ghostsecurity/reaper or check out the docs at https://ghostsecurity.github.io/reaper/
Sign up to stay up to date on future Reaper releases and news.